
Last week I managed to pass the Red Team Operator 1 exam from Zero Point Security. It was a good learning experience overall, and recommend this course to anyone intending to play around with Cobalt Strike and Active Directory testing.
The course
The course goes through the basics of the entire lifecycle of a red team engagement (planning, initial access, persistence, privilege escalation, domain reconnaissance, and etc). It uses Cobalt Strike as its Command & Control (C2) which is interesting as it is a paid product and usually used by APT groups alike.
I felt that the course materials cover many active directory attack paths (Keberos attacks, Local Administrator Password Solution, Active Directory Certificate Services, SCCM, and etc). While I had some previous knowledge from other certifications like OSCP and CRTP, it was still a good refresher, and I learned quite a bit, especially by doing it through Cobalt Strike, which I had not used before.
One thing I particularly liked was the OPSEC considerations when performing various attacks. The course also provided an Elastic instance where you can query for malicious activities.
The labs
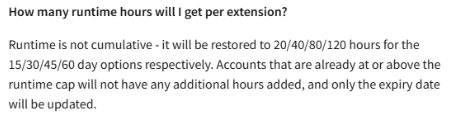
One thing to note about the labs are they are provisioned by x hours and expires in x amount of days. An example here is that the 30-day lab extension only comes with 40 hours of access, with access expiring once either condition is met. Personally, I felt that the 30 days of lab time is sufficient to clear the labs.
The labs are more of a walkthrough of the course than a challenge lab. If you follow the course, you should be able to complete the labs, as most of the learning material includes copy-and-paste commands to solve them. While the course examples are shown with Defender off, the exam has Defender enabled, so you would want to redo the labs with Defender enabled as practice for the exam.
The exam
I felt that the exam was in line with the course materials and fair. You are given 48 hours and 4 days of access in an unproctored environment. It is an assumed breach assessment where you have access to an unprivileged domain-joined workstation. Once the artifacts are configured to evade detection by Defender and have a C2 profile customised to the exam requirements, everything is set, and exploitation can begin. I ended up managing to clear the exam in the same day with all the flags. I felt that enumeration was key to success as once the attack path is mapped out, exploitation came steadily.
The conclusion
Overall, I liked the course and its entire environment. I would recommend it, as it offers lifetime access and receives regular updates. The discord community is also helpful and vibrant.
Thanks for reading this :D.